How to Spot a Fake ID: Signs, Types & Detection Tools

With the rise of digital interactions, online onboarding, and remote identity verification, the risk of encountering fake identity documents is higher than ever. Fraudsters have become more sophisticated, ranging from opportunistic individuals using borrowed IDs to organized networks producing high-quality forgeries. As identity fraud techniques evolve, staying informed about how to spot a fake ID is critical for businesses that rely on trust, compliance, and secure transactions.
Why Fake IDs Are on the Rise
The use of fake IDs is no longer limited to underage attempts to purchase alcoholic beverages, it has evolved into a complex, global threat that affects financial services, government agencies, healthcare, online platforms, and more. As identity verification becomes unavoidable in digital interactions, the incentives to forge or misuse government-issued IDs have increased dramatically.
A Shift Toward Digital Interactions
From banking and e-commerce to remote hiring and ride-sharing, identity is now verified more often through uploaded scans or live video rather than in-person checks. This shift creates opportunities for fraudsters to exploit weak or manual verification processes using digital forgeries, edited PDFs, or even deepfakes.
Wider Access to Forgery Tools
Thanks to online marketplaces and dark web communities, high-quality fake ID cards, driver licenses, and foreign passports are now easily obtainable. In some cases, buyers can even customize false identity documents to match their physical description, making detection even harder without biometric or database checks.
Economic and Criminal Motives
Fake IDs are used to commit a wide range of crimes: opening fraudulent bank accounts, hiding a criminal record, applying for government benefits, or bypassing KYC (Know Your Customer) requirements. In some cases, they’re also used to build synthetic identities that evolve over time and exploit legitimate systems.
Rising Regulatory Pressure
As fraud cases surge, so do regulations. Failing to detect a fake ID doesn’t just increase risk—it can lead to compliance violations, fines, and reputational damage. Businesses are expected to implement rigorous identity verification processes that go beyond surface-level checks.
In short, fake IDs are no longer a minor inconvenience; they’re a growing operational and compliance threat. Recognizing this evolution is the first step toward effective prevention.
Types of Fake IDs
Fake IDs come in different forms, each with varying levels of sophistication and risk.
Borrowed IDs
Borrowed IDs are a basic but common form of false identity use. In this scenario, a person uses a real ID—typically a government-issued ID such as a driver license or ID card—that belongs to someone else. This often occurs between siblings, friends, or people with similar physical features such as age, build, or hairstyle. While the document itself is authentic, it is being used by an imposter, creating a serious case of ID fraud.
These situations are particularly frequent in contexts like attempting to purchase alcoholic beverages or gain access to age-restricted venues. Because the document passes basic visual inspection, these cases can be difficult to detect—especially in manual verification environments. However, asking ID holder questions (e.g., “What’s your zip code?” or “When’s your birthday?”), checking physical description details like eye color or height, and using biometric verification or liveness detection can significantly increase the chances of identifying misuse.
Forged IDs
Forged IDs are completely fabricated documents, created from scratch to imitate authentic government-issued IDs. Unlike borrowed IDs, these are not tied to any real person or registry—they are synthetic. Criminals may produce forged ID cards, driver licenses, or even foreign passports, often incorporating convincing-looking elements like fake holograms, seals, barcodes, or other security markers.
Such IDs might contain fabricated personal details, stolen data, or slightly modified information designed to pass low-level scrutiny. Visual clues like incorrect fonts, improper alignment, or inconsistent layout spacing can signal that an ID is fake. These documents are often used by individuals trying to conceal a criminal record, create a new identity, or bypass identity checks for financial or legal gain.
The production of forged IDs has become more accessible with advancements in printing technology and access to blank templates online. This has contributed to the rise in ID fraud across multiple industries, from banking to online marketplaces.
Altered IDs
Altered IDs begin as real IDs—authentic government-issued documents, but are physically or digitally modified to mislead verifiers. Changes can include substituting the photo with another person’s, adjusting the expiration date, or tampering with personal details like name or address. These manipulations are often done on physical IDs, but can also happen in digital scans used during remote onboarding.
While more convincing than obvious forgeries, altered IDs can often be identified by checking for tampering signs such as uneven text, discoloration around the photo, or mismatched physical description details. For example, the height or eye color listed on the document may not match the person presenting it.
Altered IDs are frequently used in attempts to purchase alcoholic beverages, gain employment under a false identity, or escape background checks that might reveal a criminal record. They’re especially risky in industries dealing with foreign passports and cross-border identification, where unfamiliar formats can make manual detection harder. Automated tools that assess both visual consistency and perform backend data verification can drastically improve the detection of these modified documents.
Fake ID Forgery Methods Explained
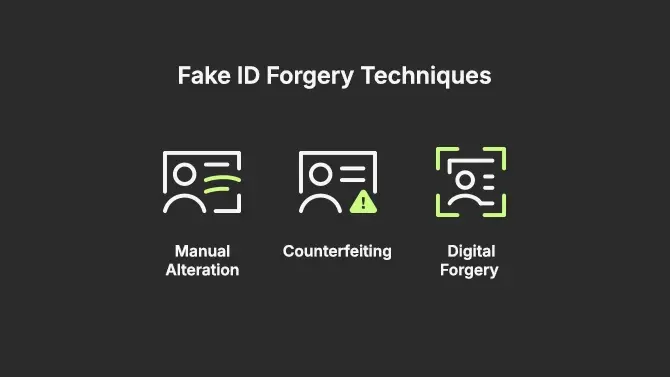
Understanding how fake IDs are made is essential to uncovering their flaws and recognizing the subtle cues that distinguish a forgery from a real ID. Each method of forgery—whether physical or digital—presents unique risks and detection challenges.
Manual Alteration
Manual alteration is a traditional but still widely used method of ID fraud. It involves tampering with a legitimate, government-issued ID, such as a driver license, ID card, or foreign passport, that may have been stolen or obtained through deception. Fraudsters manually scratch off, overwrite, or paste over key fields like names, photos, or expiration dates.
These crude alterations may bypass a cursory glance but usually fail when inspected for advanced security features. For instance, manually altered IDs often display issues with:
- Hologram alignment (e.g. mispositioned overlays or dull reflections)
- Machine Readable Zones (MRZs) that no longer match the visible data
- Signs of physical tampering such as bubbling, discoloration, or uneven lamination
Manual alteration is more common in low-tech fraud attempts but remains dangerous in settings where only visual inspection is used. Even a slight mismatch in physical description or physical features can reveal the deception, especially when paired with behavioral assessment or biometric verification.
Counterfeiting
Counterfeiting involves the complete reproduction of a fake ID from scratch. Unlike manual alteration, these documents are not based on real IDs but are fabricated using sophisticated materials and techniques that mimic official government-issued IDs. Fraudsters often use:
- Advanced printing equipment capable of replicating fonts and layouts
- UV dull paper, similar to that used in real identity documents
- Reproduced holograms, barcodes, and security stamps
Some counterfeit operations go further by using real stolen ID numbers across multiple fake documents. This tactic allows fraudsters to exploit systems that don’t cross-reference for repeated patterns—making pattern recognition a critical tool in detecting such attempts.
These high-quality fakes can appear credible to the naked eye, but automated systems that analyze document structure, security features, and MRZ consistency are far more effective at detection. Counterfeiting is often used for more serious fraud, including the creation of false identities to open bank accounts, avoid a criminal record, or exploit identity-based services.
Digital Forgery
As remote verification becomes the norm, digital forgeries have surged. These are fake IDs crafted entirely or partially using software tools, making them easy to distribute and challenging to verify without advanced systems.
Types of digital forgery include:
Edited PDFs: Scanned copies of real IDs are altered in image editing tools to change names, photos, or dates. These are then submitted via email or upload portals, often during remote onboarding or online purchases.
Synthetic Identities: These combine real and fake information—like a real name with a fake birthdate or address—to create an entirely new persona. This tactic can be used to build a false identity that slips past basic checks, often avoiding detection unless cross-referenced with official databases.
Deepfakes: Powered by AI, deepfakes present a new frontier in identity fraud. Fraudsters can impersonate someone during a live verification check by generating a realistic video that mimics their appearance and voice. This method is particularly dangerous in environments relying on real-time selfie video or facial recognition without additional safeguards.
Digital forgeries require robust verification systems that include liveness detection, facial matching, and data cross-checking against authoritative sources. Without these, digital ID submissions can easily be manipulated to pass as valid.

How to Spot a Fake ID
The important thing to remember when talking about spotting a fake document is that there’s a need to distinguish between manual and automated identity verification.
Manual Identity Verification
This includes people checking identity documents. That may be as simple as a bartender asking for a document to confirm a person is of age and as complicated as a bank teller spending hours or even days to confirm that all provided information is accurate.
Although acceptable in some cases, manual identification relies on primitive methods that not only take much longer, but focus heavily on simpler visual clues. On top of this, manual identification is prone to human error.
Automated Identity Verification
On the other side of the process, we have automated identification. With a good system, this can take as little as 60 seconds. It involves AI algorithms that can easily double-check any data with governmental registries, performs liveness checks to guard against deepfakes and can easily read MRZs.
Automated identity verification systems employ various techniques to spot fake IDs. Here are some common methods:
Security Features Analysis: Advanced identity verification systems use AI to analyse security features such as MRZs, UVs and holograms for consistency and authenticity.
Document Structure Analysis: AI algorithms examine the overall structure of ID documents, including the arrangement of information, fonts, and design elements. Deviations from standard patterns found in genuine documents can indicate potential forgeries.
Pattern Recognition: Identity verification systems leverage pattern recognition to identify anomalies in the layout and formatting of documents. This includes analysing the placement of text, images, and other elements to detect irregularities that may be indicative of a fake ID.
Face Matching and Biometrics: Systems use facial recognition technology to match the person’s face on the ID with a live image or a previously captured image during the verification process. Biometric data, such as fingerprints or iris scans, can also be employed for additional verification.
Data Verification: Cross-referencing the information on the ID with external databases and sources helps verify the accuracy of the provided details. Inconsistencies or discrepancies in the data, such as mismatched names or addresses, can signal potential fraud.
Machine Learning for Anomaly Detection: Identity verification systems often incorporate machine learning algorithms that learn from vast datasets to identify subtle patterns associated with authentic IDs. This allows the system to adapt and improve its ability to detect new and evolving methods of forgery.
Visual Inspection
Look for inconsistencies in:
- Fonts and layout
- Holograms or watermarks
- Photo clarity and alignment
- MRZ codes and expiration dates
Functional Check
Test the ID’s functionality by:
- Scanning barcodes or MRZs
- Running UV light over security features
- Cross-referencing data with government databases (where possible)
Behavioral Signs
Sometimes the person presenting the ID can give themselves away. Watch for:
- Nervousness or evasiveness
- Inability to answer basic personal questions
- Delayed responses during real-time verification
Ondato’s Tools for Detecting Fake IDs

Although telling legitimate and fake IDs apart can be tricky when done manually, Ondato’s automated identity verification solution can ensure 99.8% accuracy. On top of this, it provides:
Regulatory Compliance:
Our automated identity verification solution can assist companies in meeting regulatory compliance requirements. By ensuring a robust and standardised verification process, we help organisations adhere to industry regulations and prevent legal complications.
Cost Savings:
The long-term benefits of Ondato include cost savings for your company. The efficiency and accuracy of automated systems reduce the need for extensive manual labour and can cut KYC-related costs by up to 90%.
Efficiency and Speed:
Automation allows for swift document verification, enabling companies to process large volumes of identification documents quickly. Ondato’s solution takes just 60 seconds to confirm the identity of your clients. This efficiency is particularly crucial in industries where time-sensitive decisions are required, such as financial services or security.
Advanced Technology:
At Ondato, we leverage advanced technologies, such as machine learning and artificial intelligence, to detect sophisticated forgery techniques. These technologies can identify subtle inconsistencies that might be challenging for human eyes to notice.
Comprehensive Analysis:
Our solution can analyse various aspects of a document simultaneously, including fonts, holograms, UV features, and more. This comprehensive analysis ensures a thorough examination of the document for signs of forgery, enhancing overall security.
Reduced Human Error:
Human judgement can be influenced by various factors, including fatigue, stress, or preconceived notions. Automated systems eliminate such biases, providing an objective and impartial assessment of IDs.
Final Thoughts on Fake ID Detection
Fake IDs are becoming more convincing, but so are the tools to detect them. By understanding the types of forgeries and implementing a mix of visual checks, behavioral awareness, and automated tools, businesses can stay ahead of fraud and protect their operations.









